How to block XMLRPC Attacks using CSF
We will need to create custom log from which CSF will be able to search for wp-login.php and xmlrpc.php requests.
Now, edit your ecsf.conf
nano /etc/csf/csf.conf
locate the line: CUSTOM1_LOG = "/var/log/customlog"
and replace it with: CUSTOM1_LOG = "/usr/local/apache/domlogs/*/*"Have a look :

Now, create a function within CSF to detect and block these attacks.
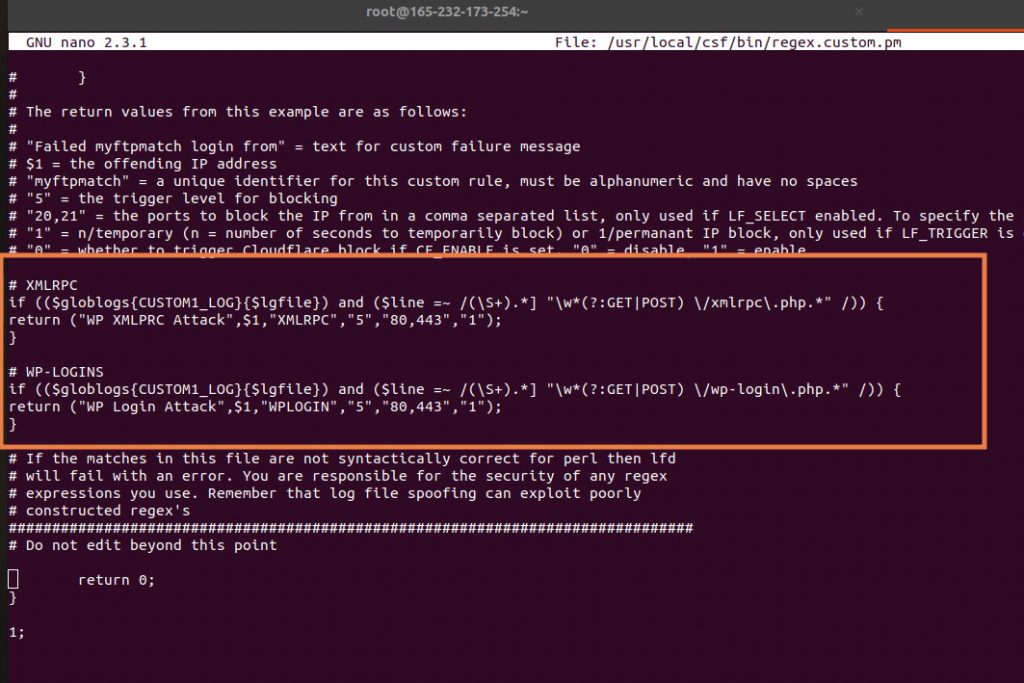
nano /usr/local/csf/bin/regex.custom.pm
Add the following code:
# Block IP if more than 5 requests in 3600 for wp-login
if (($globlogs{CUSTOM1_LOG}{$lgfile}) and ($line =~ /(\S+).*] "\w*(?:GET|POST) \/wp-login\.php.*" /)) {
return ("WP Login Attack",$1,"WPLOGIN","5","80,443","1");
}
# Block IP if more than 5 requests in 3600 for xml-rpc
if (($globlogs{CUSTOM1_LOG}{$lgfile}) and ($line =~ /(\S+).*] "\w*(?:GET|POST) \/xmlrpc\.php.*" /)) {
return ("WP XMLPRC Attack",$1,"XMLRPC","5","80,443","1");
}
have a look :
Restart CSF and LFD to apply changed:
csf -r service lfd restart


