GHOST vulnerability affecting Linux systems was discovered in the C library of GNU / Linux (glibc) that gives control to attackers without requiring system credentials.
GHOST creates a buffer overflow that affects all the gethostbyname*() functions in the glibc library. These functions change a hostname into an IP addresses. A hacker exploiting this can gain complete access of the Linux machine.
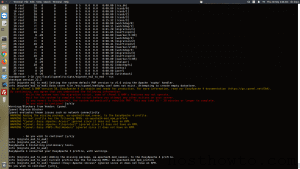
To verify you are running the updated packages, run the following commands:
rpm -qa glibc
rpm -qa nscd
The updated versions for CentOS 5 and 6 are shown below:
####
CentOS 5:
glibc-2.5-123.el5_11.1
nscd-2.5-123.el5_11.1
CentOS 6:
glibc-2.12-1.149.el6_6.5
nscd-2.12-1.149.el6_6.5
####
Not on these versions of CentOS? Run “yum update glibc nscd” to update the package.
A server reboot is recommended to ensure that all services begin using the new packages. If a reboot is not possible, most processes should be restarted on the server.