Symlink Protection for cPanel
Symlink Protection for cPanel is much important . Symlink attack occurs after the attacker has been able to read the contents of the /etc/passwd file and has enumerated the server’s users.
Symlink race condition vulnerability
If you enable both of the SymLinksIfOwnerMatch and FollowSymLinks configuration settings, Apache becomes vulnerable to a race condition through symlinks. This symlink vulnerability allows a malicious user to serve files from anywhere on a server that strict OS-level permissions do not protect.
Filesystem-level solutions : Enable mod_ruid + jailshell for your apache webserver.
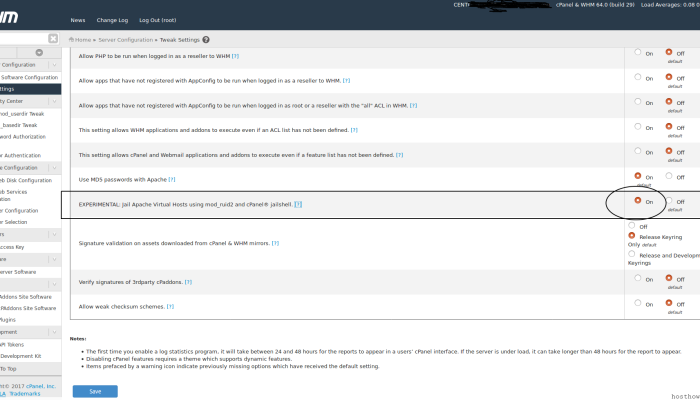
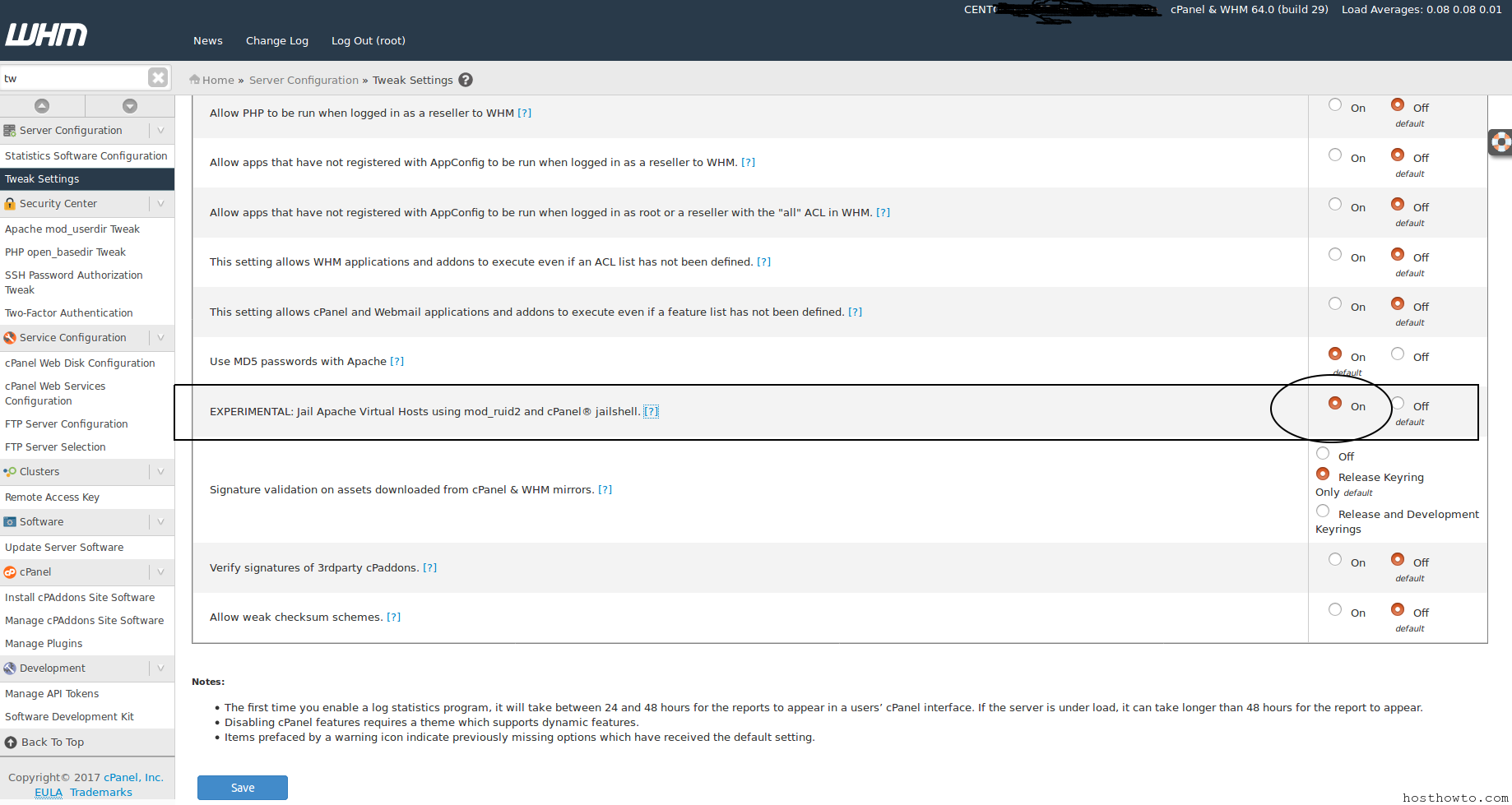
To enable this option, recompile Apache and then enable EXPERIMENTAL: Jailshell Virtual Hosts using mod_ruid2 and cPanel jailshell in WHM’s Tweak Settings interface (Home >> Server Configuration >> Tweak Settings).
Using cageFS
CageFS is a virtualized file system and a set of tools to contain each user in its own ‘cage’. This option is available on all cPanel-supported platforms today, and it is already included with CloudLinux.